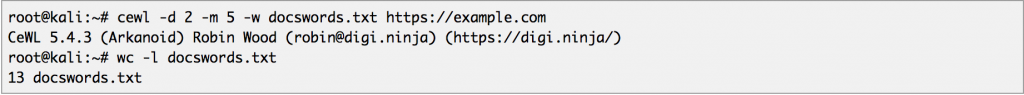
We can generate a list of potential password to be used for bruteforcing using a tool called CeWL.
Usage Example:
Scan to a depth of 2 (-d 2) and use a minimum word length of 5 (-m 5), save the words to a file (-w docswords.txt), targeting the given URL (https://example.com):