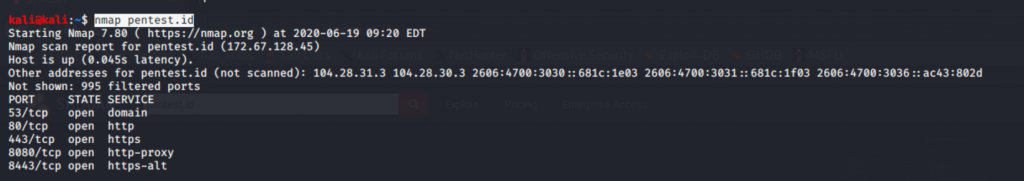
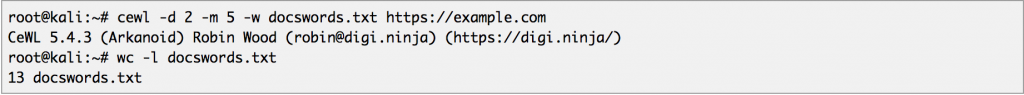
This tutorial is 100% for Education Purpose only. Any time the word “Hacking” that is used on this site shall be regarded as Ethical Hacking. Do not attempt to violate the law with anything contained here. If you planned to use the content for illegal purposes, then please leave this site immediately! We will not be responsible for any illegal actions.
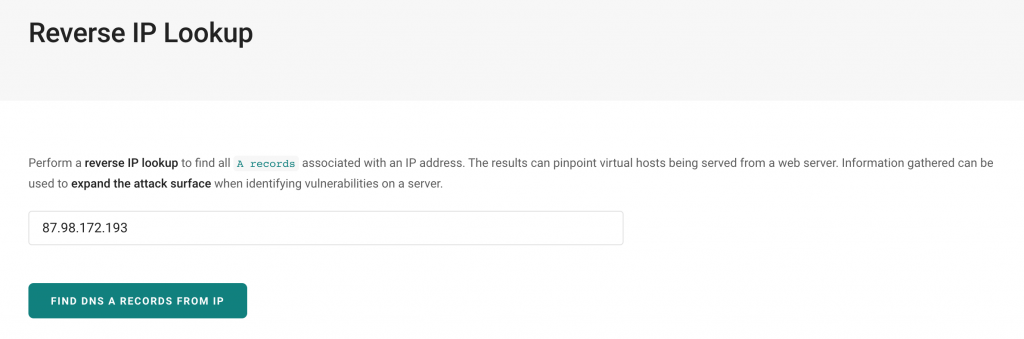
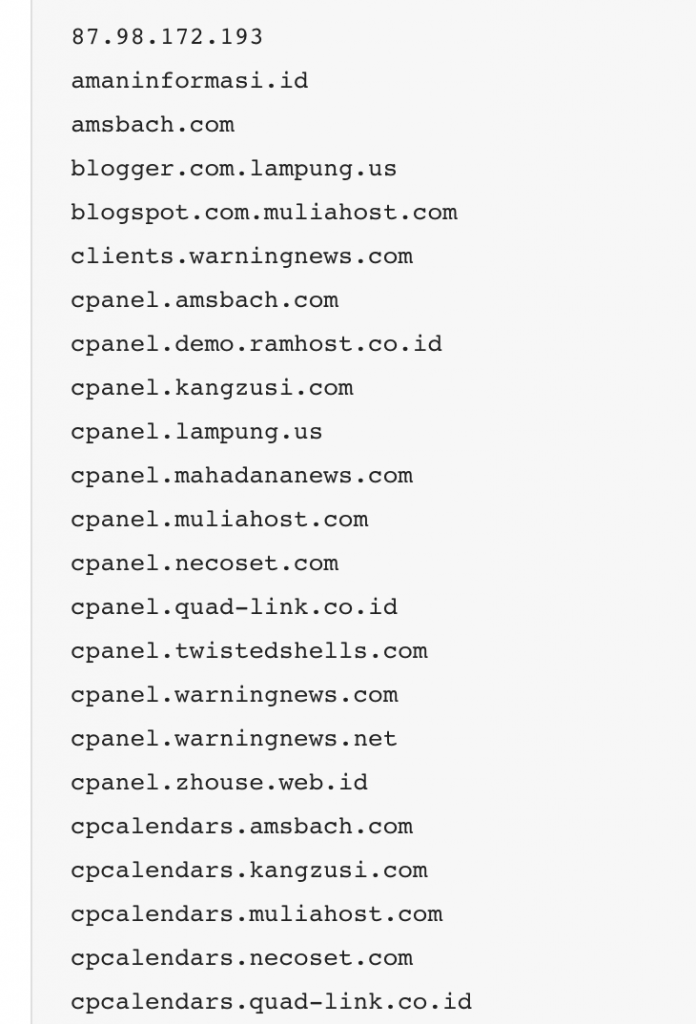
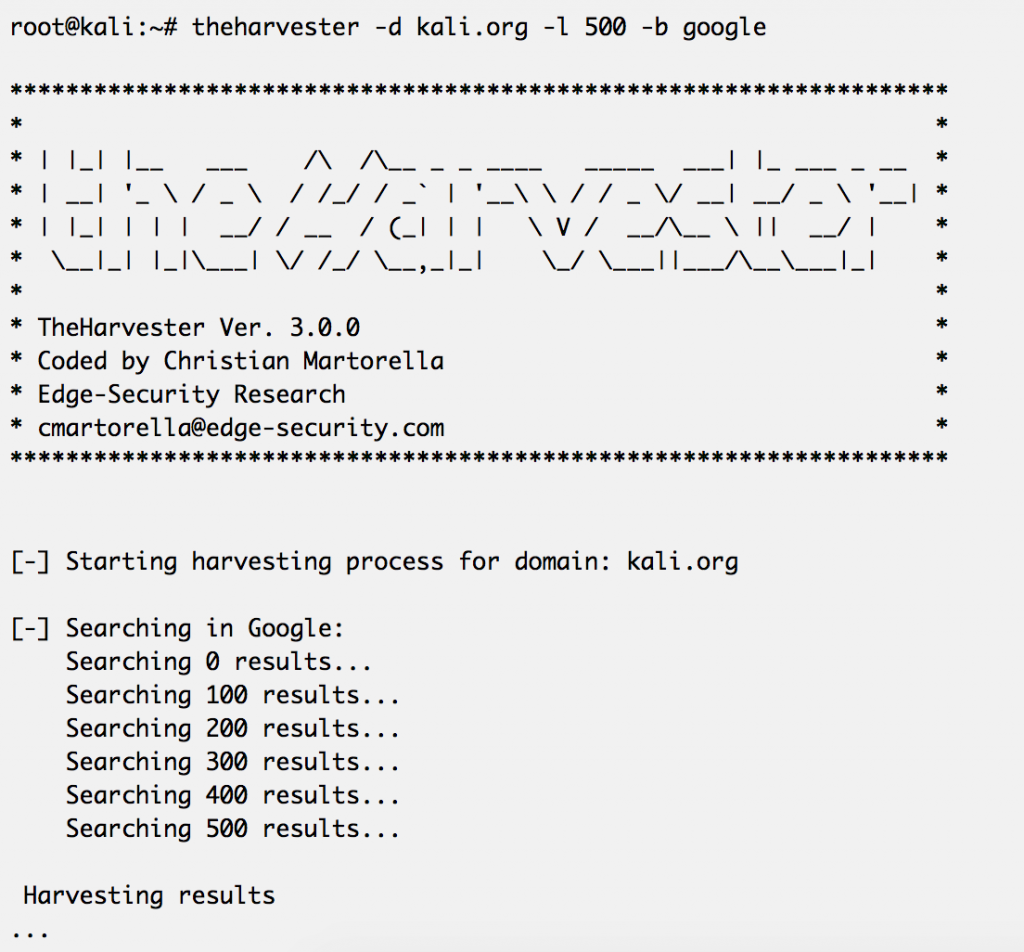
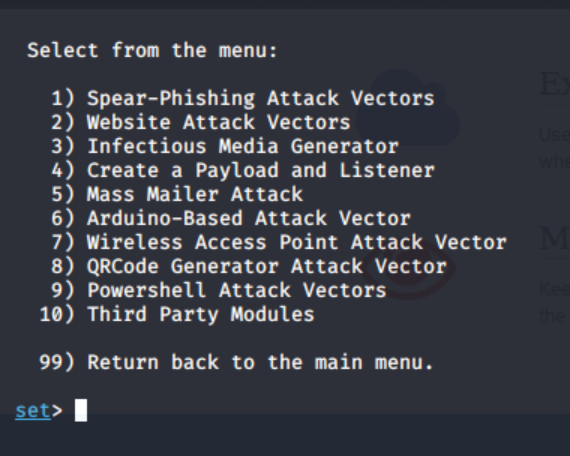
Google “Dorking” is the practice of using Google to find vulnerable web applications and servers by using native Google search engine capabilities. Unless you block specific resources from your website using a robots. txt file, Google indexes all the information that is present on any website.
Ex:
Finding misconfigured Laravel Applicationsindex of ".env"
Finding misconfigured servers that have “ktp” filesindex of "ktp"
Finding misconfigured servers that have “kk” filesindex of "kk"
Searches for specified term in the URL.
For example:inurl:register.php
Read More:
Documentation of Google Dorks: https://www.exploit-db.com/google-hacking-database